TryHackMe: OSINT Challenge

Write Up of TryHackMe’s OSINT Challenge, tracing a digital footprint using real-world OSINT techniques.
🇧🇷 Ler em Português.
TryHackMe: OSINT Challenge
Full Write Up & Guide
This is a complete walkthrough of the OSINT Challenge hosted on TryHackMe, a popular cybersecurity learning platform. This open-source intelligence (OSINT) room challenges users to trace a fictional character’s digital footprint, starting from a single image.
Throughout the challenge, you'll extract metadata, perform reverse image searches, investigate social media activity, and explore GitHub repositories to uncover hidden flags—one of which is cleverly embedded in an interactive element on a personal blog. Perfect for cybersecurity newbies and digital investigators, this hands-on Capture The Flag (CTF) provides OSINT training using real-world techniques.
Whether you're preparing for a cybersecurity career, studying for OSINT certifications, or just love solving online puzzles, this room is a great way to boost your reconnaissance skills and learn how to track someone online using only publicly available data.
Access room here:
👉 https://tryhackme.com/room/desafioosint
Task 1 - OSINT: Image
The challenge starts with an image. Your mission: extract metadata and find clues that reveal the photo's location.
| Questions |
|---|
| Q1. What is the username? |
| Q2. What is the User’s full name? |
| Q3. Where was the photo taken? |
Q1. What is the username?
To retrieve image metadata, you can use various online EXIF viewers. On Linux systems, the exiftool command is ideal:
exiftool <filename>
If it's not installed, run:
sudo apt install exiftool
☝️🤓 For other platforms, follow the Installation Guide.

Q2. What is the User’s full name?
By continuing to analyze the metadata, you’ll uncover the user’s real name. Always look carefully at fields like Author, Artist, Creator, Copyright and Owner:

Q3. Where was the photo taken?
Drop the image on Google:
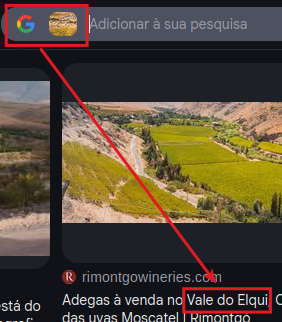
🇧🇷 This challenge is in Portuguese, so remember to translate and interpret clues accordingly.
Task 2 - OSINT: Social Media
Now that you have the username and full name, start your social media investigation. Use platforms like Facebook, Instagram, X (Twitter), and LinkedIn to track down personal details.
| Questions |
|---|
| Q1. What is the user’s city of birth? |
| Q2. Where was the user on May 13, 2024? |
| Q3. What is the user’s email? |
Q1. What is the user’s city of birth?
Look at the user’s public profiles. Facebook and LinkedIn often contain biographical details like the city of birth or hometown.
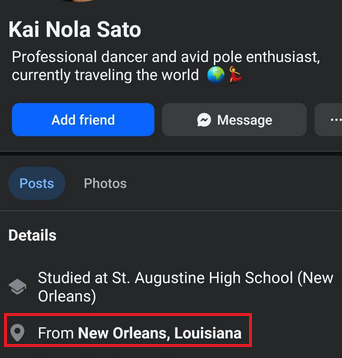
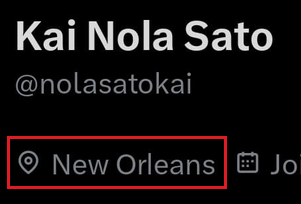
☝️🤓 Again: This challenge is in Portuguese, so remember to translate and interpret clues accordingly.
Q2. Where was the user on May 13, 2024?
Scroll through social media posts and geotagged photos. Users often share travel details or check-ins that reveal their location.

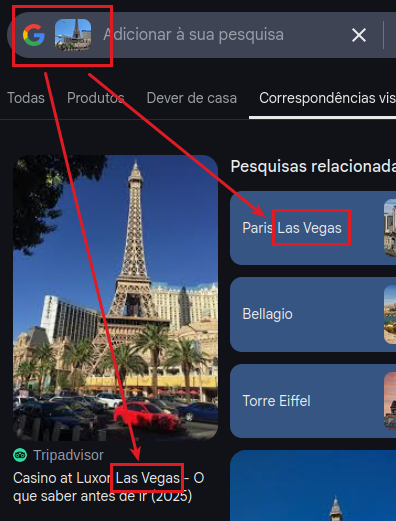
Q3. What is the user’s email?
GitHub can be a goldmine for OSINT. Check commits and profile settings to uncover the user’s email address.
Task 3 - First Flag: Welcome to the CSSDC OSINT CTF
Now that you have several user data, look for the first flag.
| Question |
|---|
| Q1. What flag is found in the repository? |
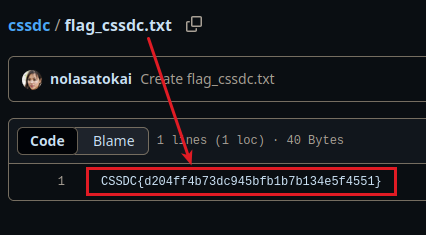
Q1. What flag is found in the repository?
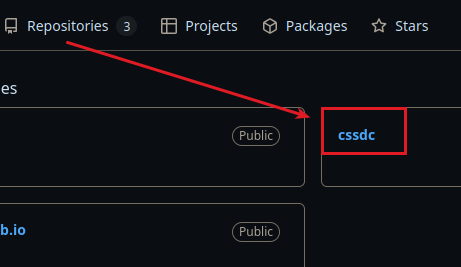
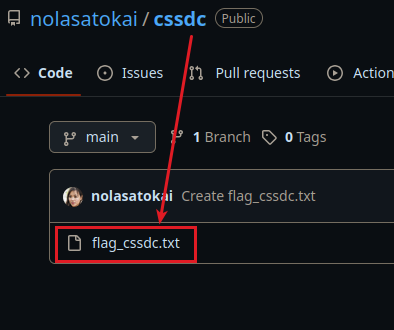
Now that we’ve gathered some personal data, the first flag is hidden inside a GitHub repository. Look for a repo named "cssdc", as referenced in the challenge description.
Task 4 - Final Flag
Continue collecting more data from the user and find the last flag on the user's personal page.
| Questions |
|---|
| Q1. What is the user’s blog address? |
| Q2. Which database does the website use? |
| Q3. Search for the Flag on the Website. |
Q1. What is the user’s blog address?
Most GitHub profiles include personal websites or blogs in the bio section. You’ll find the link easily.
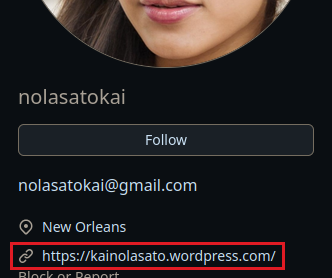
Q2. Which database does the website use?
Use tools like Wappalyzer to analyze the site’s backend technologies.
☝️🤓 Install Wappalyzer as a browser extension.

Q3. Search for the Flag on the Website.
Click around every element on the blog. Hover over unusual elements and inspect hidden content or embedded text.
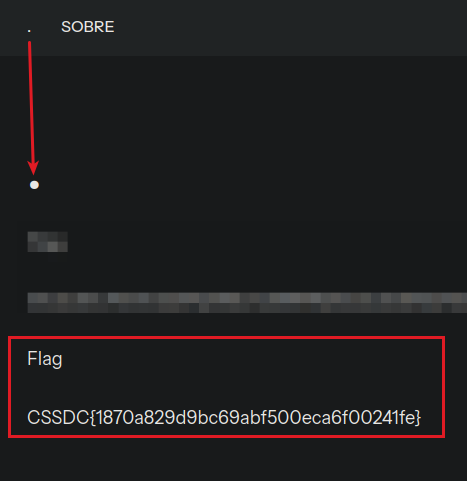
🎉 Congratulations! All Tasks Completed!

You’ve successfully completed the TryHackMe OSINT Challenge. This room is an excellent introduction to practical OSINT and digital forensics, teaching how to gather and analyze open-source information across multiple platforms.
🚩 Ready for your next TryHackMe adventure?

If you find this post helpful, please consider sharing 💜
