CVE-2025-9144

Stored XSS in Scada-LTS: Input Validation Flaw in Publisher Name Field
🇧🇷 Ler em Português.
CVE-2025-9144
Introduction
While testing the Scada-LTS application, I discovered a stored Cross-Site Scripting (XSS) vulnerability in the publisher_edit.shtm endpoint. The flaw lies in the name parameter, which fails to sanitize user input properly. As a result, an attacker can inject malicious JavaScript that is executed whenever the publishers.shtm page is loaded.In this post, I’ll walk you through the technical details and the exact payload used to demonstrate the issue.
What is CVE-2025-9144?
CVE-2025-9144 refers to a stored XSS vulnerability caused by insufficient input validation in the name parameter of the publisher_edit.shtm endpoint. The unsanitized input is stored on the server and executed automatically in the browser when the corresponding listing page is accessed.
Technical Details
➤ Vulnerable Endpoint publisher_edit.shtm
➤ Affected Parameter: name
➤ Trigger Page: publishers.shtm
➤ Payload Used
<img src=x onerror=alert(32)>
Proof of Concept (PoC)
Here’s how you can reproduce the vulnerability step by step:
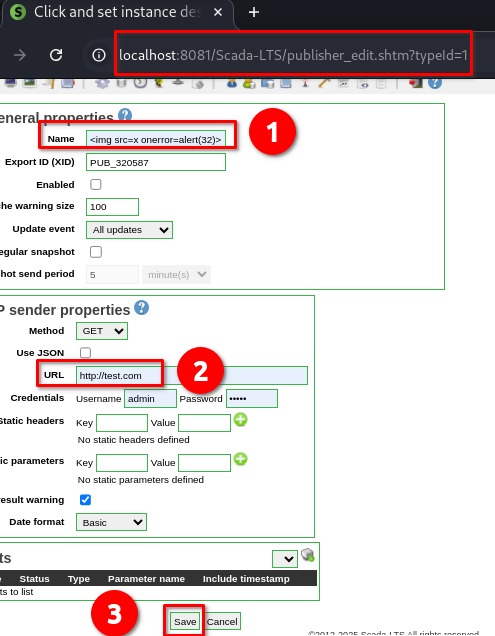
➤ Navigate to: publisher_edit.shtm
➤ In the first field labeled “Name”, insert the payload
➤ In the fifth field (“URL”), insert an URL, such as: test.com
➤ Scroll down and click the “Save” button
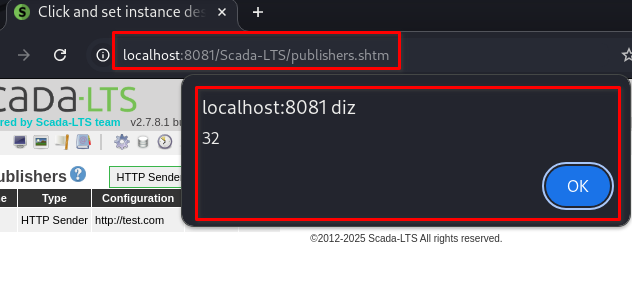
After saving, the application redirects or lists entries on
publishers.shtm, where the malicious script is automatically executed in the browser of any user who visits the page.
Parameter name |
|---|
 |
You can access the full report and see the complete step-by-step here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The vulnerability was reported ethically and assigned as:
Conclusion
Even a single input field without proper validation can open the door to high-impact attacks.CVE-2025-9144 highlights the importance of input sanitization at every stage of development. If you work with web applications, it’s important to review all user entry points carefully.Simple oversights like this one can easily go unnoticed but carry serious risks.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜