CVE-2025-9143

Three XSS in One Page? Scada-LTS Fails to Sanitize Inputs in Mailing List Settings
🇧🇷 Ler em Português.
CVE-2025-9143
Introduction
While exploring the mailing list configuration section of Scada-LTS, I stumbled upon something that immediately raised a red flag: three separate fields on the same page were vulnerable to stored XSS.In this post, I’ll guide you through what I found in the mailing_lists.shtm endpoint, how each vector works, and why this kind of oversight can have severe consequences — especially in software used to control industrial systems.
What is CVE-2025-9143?
CVE-2025-9143 refers to a set of Stored Cross-Site Scripting (XSS) vulnerabilities in the Scada-LTS application, specifically affecting the mailing_lists.shtm endpoint.The issue stems from three different parameters (name, userList, and address) that accept user input without proper sanitization. When any of these fields are filled with a malicious payload, the code gets stored on the server and automatically executed in the browser of anyone who accesses the page.
Technical Details
➤ Vulnerable Endpoint mailing_lists.shtm
➤ Affected Parameters: name, userList and address
➤ Payload Used
<img src=x onerror=alert(40)>
Proof of Concept (PoC)
Here’s how you can reproduce the vulnerability step by step:
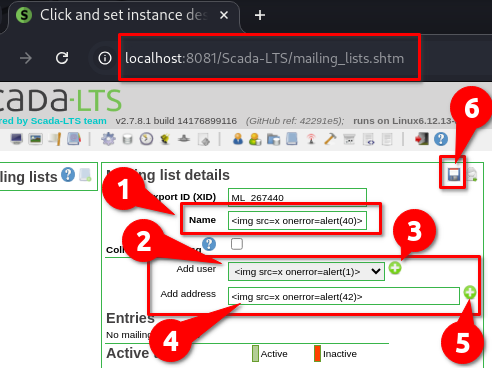
➤ Navigate to: mailing_lists.shtm
➤ Field “Name”: Paste the payload into the second field labeled “Name”
➤ Field “Add user”:
Go to
users.shtmand create a user whose name includes the payloadReturn to
mailing_lists.shtmand select that user, click on “+”
➤ Field “Add address”:
Paste the same payload into the “Add address” field
Click “+” to add it
➤ Click the disk icon to save
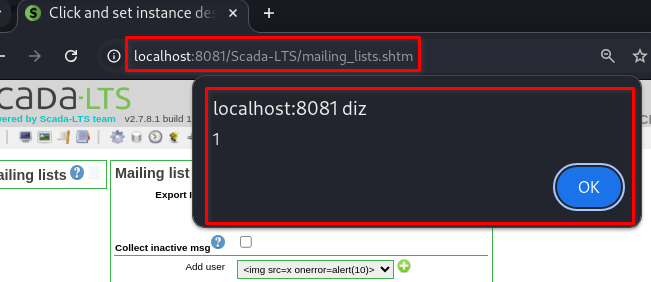
All payloads are now stored and will trigger on page load.
Parameter name | Parameter userList |
|---|---|
 | 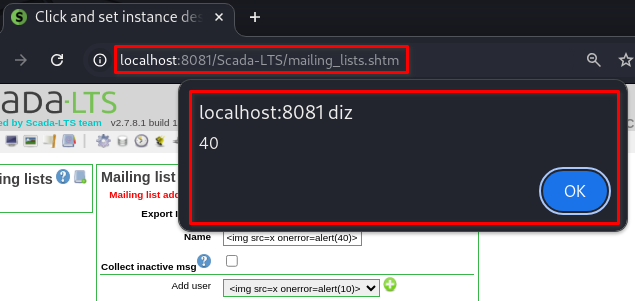 |
Parameter address |
|---|
 |
You can access the full report and see the complete step-by-step here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The vulnerability was reported ethically and assigned as:
Conclusion
Even a single input field without proper validation can open the door to high-impact attacks.CVE-2025-9143 highlights the importance of input sanitization at every stage of development. If you work with web applications, it’s important to review all user entry points carefully.Simple oversights like this one can easily go unnoticed but carry serious risks.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜