CVE-2025-8545
Stored XSS in i-Educar via educar_motivo_afastamento_cad.php (with PoC and Screenshots)
🇧🇷 Ler em Português.
CVE-2025-8545
Introduction
While exploring the module responsible for managing leave reasons in the i-Educar system, I discovered a stored XSS vulnerability in the /intranet/educar_motivo_afastamento_cad.php endpoint. The nm_motivo parameter — used to define reasons for school absences — allows the injection of malicious scripts without any sanitization.These scripts are stored in the database and executed automatically when the corresponding listing page is accessed.In this post, I’ll walk you through the technical details, how the vulnerability was exploited (PoC), screenshots with real evidence, and the security risks it represents in real-world environments.
What is CVE-2025-8545?
The CVE-2025-8545 is a Stored Cross-Site Scripting (XSS) vulnerability found in the /intranet/educar_motivo_afastamento_cad.php endpoint of the i-Educar application.The nm_motivo parameter fails to properly validate user inputs, allowing attackers to persist JavaScript payloads on the server. The malicious code is executed when the /intranet/educar_motivo_afastamento_lst.php page is loaded, impacting any user who visits it.
Technical Details
➤ Vulnerable Endpoint: /intranet/educar_motivo_afastamento_cad.php
➤ Affected Parameter: nm_motivo
➤ Trigger Page: /intranet/educar_motivo_afastamento_lst.php
➤ Payload Used
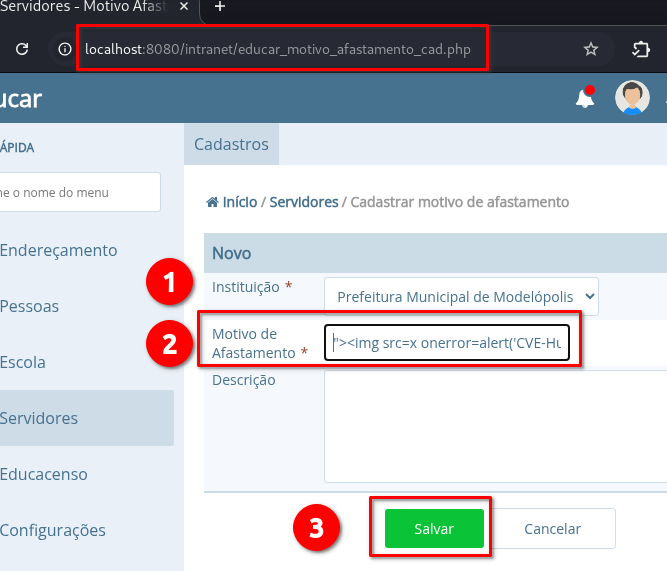
"><img src=x onerror=alert('CVE-Hunters')>
Proof of Concept (PoC)
To reproduce the vulnerability:
➤ Access the endpoint: /intranet/educar_motivo_afastamento_cad.php
➤ Select the default option in the “Instituição” field
➤ Insert the payload in the “Motivo de Afastamento” field
➤ Click on: “Salvar”
The
/intranet/educar_motivo_afastamento_lst.phppage will automatically load, triggering the malicious payload:
Parameter nm_motivo |
|---|
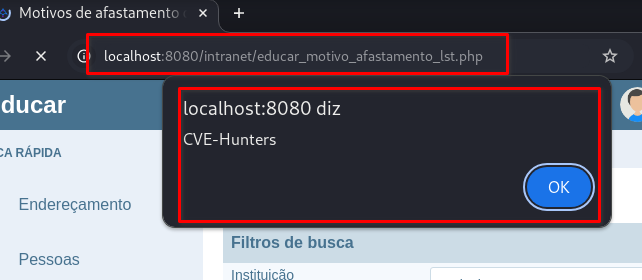 |
You can access the full technical report with all step-by-step evidence here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
This vulnerability was reported responsibly and is publicly registered as:
Conclusion
CVE-2025-8545 shows how even seemingly harmless fields — like a simple reason for school absence — can become serious entry points for attacks if user input isn't properly sanitized.Educational systems must implement secure development practices across the entire application lifecycle, especially when dealing with sensitive data.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜