CVE-2025-8544

Stored XSS in i-Educar via RegraAvaliacao/edit (With PoC and Screenshots)
🇧🇷 Ler em Português.
CVE-2025-8544
Introduction
While analyzing the grading rules feature in the i-Educar system, I found a stored XSS vulnerability in the /module/RegraAvaliacao/edit endpoint. The nome parameter — responsible for storing the name of a grading rule — accepts JavaScript payloads without any input sanitization or validation.The injected script is stored on the server and automatically executed when the grading rules listing page is accessed.In this post, I’ll show how the vulnerability was exploited in practice, including a step-by-step Proof of Concept (PoC), screenshots, and an overview of the potential real-world impact this flaw introduces.
What is CVE-2025-8544?
CVE-2025-8544 refers to a stored Cross-Site Scripting (XSS) vulnerability in the /module/RegraAvaliacao/edit endpoint of the i-Educar application.The issue lies in the nome parameter, which defines the name of a grading rule. When malicious JavaScript is injected into this field, it is saved on the server and executed automatically when users access the /module/RegraAvaliacao/index page.
Technical Details
➤ Vulnerable Endpoint: /module/RegraAvaliacao/edit
➤ Affected Parameter: nome
➤ Trigger Page: /module/RegraAvaliacao/index
➤ Payload Used
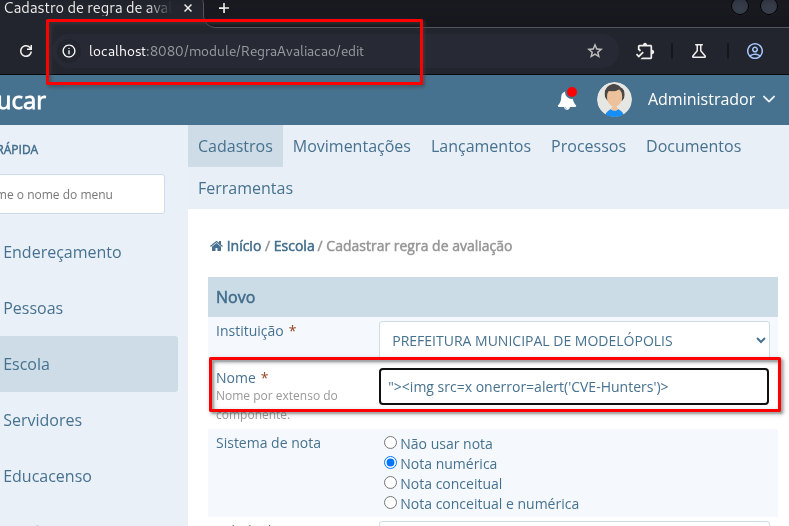
"><img src=x onerror=alert('CVE-Hunters')>
Proof of Concept (PoC)
To reproduce the vulnerability:
➤ Access the endpoint: /module/RegraAvaliacao/edit
➤ Insert the payload in the second field: “Nome”
➤ Fill out the other required fields with any value
➤ Click on: “Salvar”
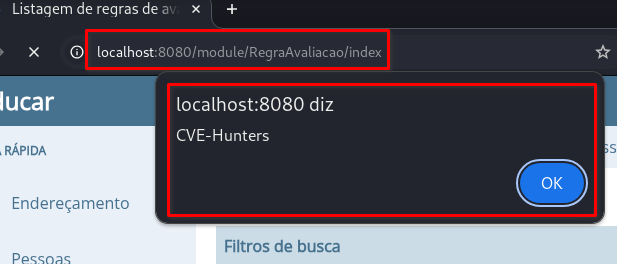
The
/module/RegraAvaliacao/indexpage will load automatically and the payload will be triggered:
Parameter nome |
|---|
 |
You can view the full technical report here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The vulnerability was ethically reported and published as:
Conclusion
CVE-2025-8544 shows how even simple administrative fields — like the name of a grading rule — can become attack vectors when input validation is missing.It's essential to apply strict input validation and output encoding across the entire application, especially in admin interfaces where the consequences of XSS would be severe.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜