CVE-2025-8543

Stored XSS in i-Educar via educar_raca_cad.php (With PoC and Screenshots)
🇧🇷 Ler em Português.
CVE-2025-8543
Introduction
While reviewing the ethnic group classification module of the i-Educar system, I discovered a stored XSS vulnerability in the /intranet/educar_raca_cad.php endpoint. The nm_raca parameter — responsible for registering a person’s ethnic group — fails to sanitize user input, allowing malicious scripts to be injected and stored on the server. When the ethnic group listing page is accessed, the payload is executed automatically, potentially compromising user data.In this post, I’ll show how the vulnerability was identified and exploited in practice, including a working Proof of Concept (PoC), screenshots of the execution, and a breakdown of the real-world risks this flaw can introduce to production environments.
What is CVE-2025-8543?
CVE-2025-8543 is a stored Cross-Site Scripting (XSS) vulnerability found in the /intranet/educar_raca_cad.php endpoint of the i-Educar application.The vulnerability affects the nm_raca parameter, which is used to define a person’s ethnic group. When unsanitized input is saved, it becomes a persistent attack vector that is triggered on the page /intranet/educar_raca_lst.php.
Technical Details
➤ Vulnerable Endpoint: /intranet/educar_raca_cad.php
➤ Affected Parameter: nm_raca
➤ Trigger Page: /intranet/educar_raca_lst.php
➤ Payload Used
"><img src=x onerror=alert('CVE-Hunters')>
Proof of Concept (PoC)
To reproduce this vulnerability, follow the steps below:
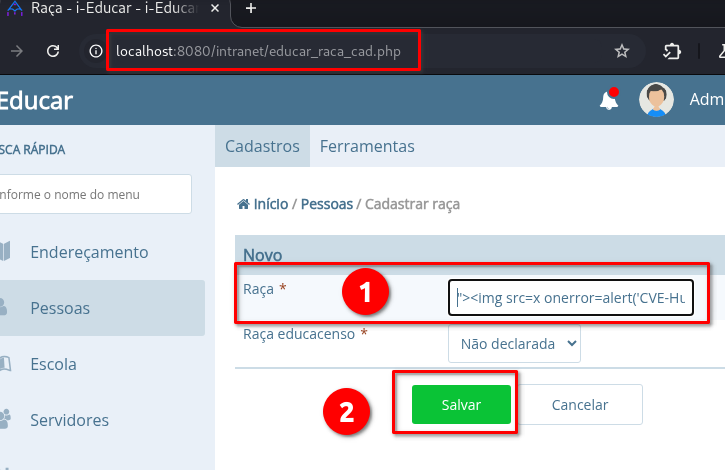
➤ Access the endpoint: /intranet/educar_raca_cad.php
➤ Insert the payload in the “Raça” (Ethnic Group) field Nome
➤ Click on: “Salvar”
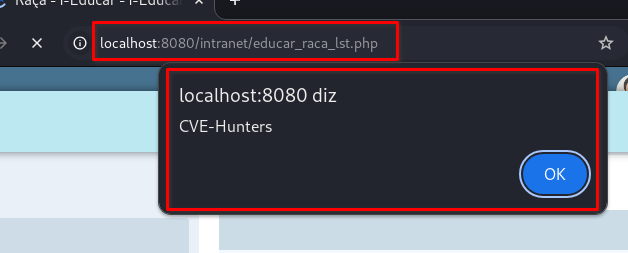
The
/intranet/educar_raca_lst.phppage will automatically load and execute the XSS:
Parameter nm_raca |
|---|
 |
You can view the full technical report here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The vulnerability was ethically reported and published as:
Conclusion
CVE-2025-8543 reinforces that all input fields — even those related to demographic data like ethnic group — must be properly validated and encoded.Ignoring sanitization on administrative pages creates long-lasting security issues that are easily exploitable. Always treat user input as untrusted.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜