CVE-2025-8542

How I Discovered Multiple Stored XSS in i-Educar via empresas_cad.php (With PoC and Screenshots)
🇧🇷 Ler em Português.
CVE-2025-8542
Introduction
While analyzing the company registration functionality in the i-Educar system, I found multiple stored XSS vulnerabilities in the /intranet/empresas_cad.php endpoint. Both the fantasia and razão social fields accepted malicious scripts without any input sanitization.As a result, the payload was saved on the server and executed automatically when accessing the company listing page. This vulnerability was officially assigned as CVE-2025-8542.In this post, I’ll walk you through the technical details, PoC steps, and security risks posed by this issue.
What is CVE-2025-8542?
CVE-2025-8542 refers two stored Cross-Site Scripting (XSS) vulnerabilities in the /intranet/empresas_cad.php endpoint of the i-Educar application.The fantasia and razão social parameters fail to properly sanitize user input, allowing malicious scripts to be stored and automatically executed when the /intranet/empresas_lst.php page is accessed.
Technical Details
➤ Vulnerable Endpoint /intranet/empresas_cad.php
➤ Affected Parameters: fantasia, razao_social
➤ Trigger Page: /intranet/empresas_lst.php
➤ Payload Used
<img src=x onerror=alert(1)>
Proof of Concept (PoC)
To reproduce this vulnerability, follow the steps below:
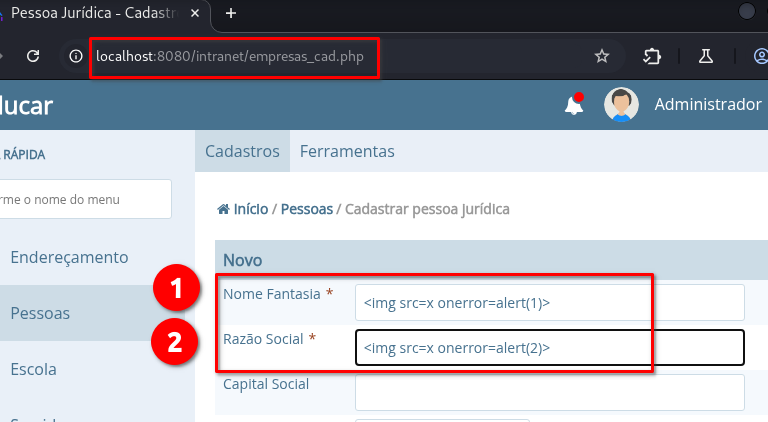
➤ Access the endpoint: /intranet/empresas_cad.php
➤ Insert the payload in both fields: “Nome Fantasia” and “Razão Social”
➤ The other fields can be left empty
➤ Click on: “Salvar”
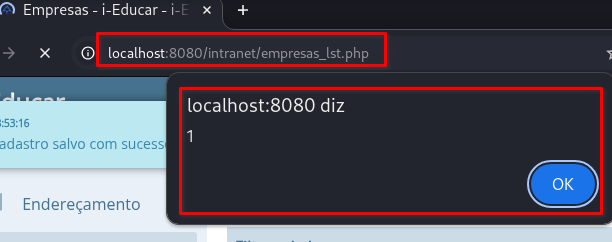
The
/intranet/empresas_lst.phppage will load automatically, triggering the stored XSS:
Parameter fantasia | Parameter razao_social |
|---|---|
 | 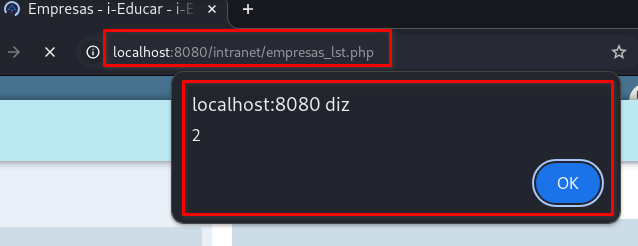 |
You can access the full technical report with all PoC steps here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The issue was ethically reported and officially registered as:
Conclusion
CVE-2025-8542 shows that even seemingly harmless fields like company names can become vectors for stored XSS attacks. When displayed in administrative panels without proper validation or output encoding, they pose a real threat.Ensuring input validation on every form — no matter how trivial the field — is important to keeping web applications secure.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜