CVE-2025-8541
Stored XSS in i-Educar via public_uf_cad.php (With PoC and Screenshots)
🇧🇷 Ler em Português.
CVE-2025-8541
Introduction
While reviewing the federal unit module in the i-Educar system, I identified yet another stored XSS vulnerability — this time in the /intranet/public_uf_cad.php endpoint. The nome parameter accepts and stores malicious scripts without any input sanitization.Once submitted, the payload is automatically executed when the federal unit listing page is accessed. This vulnerability was officially assigned as CVE-2025-8541.Below, I break down the technical details, PoC steps, and real-world risks involved.
What is CVE-2025-8541?
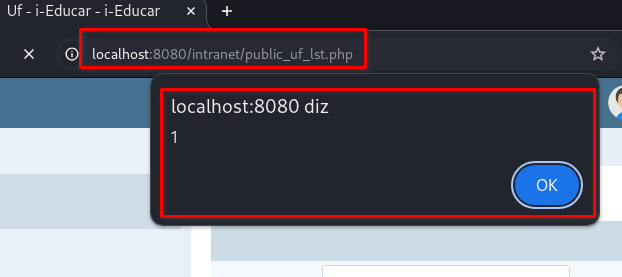
CVE-2025-8541 is a stored Cross-Site Scripting (XSS) vulnerability located in the /intranet/public_uf_cad.php endpoint of the i-Educar application.The flaw allows attackers to inject scripts into the nome field, which are then stored on the server and executed automatically when the page /intranet/public_uf_lst.php is accessed by users.
Technical Details
➤ Vulnerable Endpoint: /intranet/public_uf_cad.php
➤ Affected Parameter: nome
➤ Trigger Page: /intranet/public_uf_lst.php
➤ Payload Used
<img src=x onerror=alert(1)>
Proof of Concept (PoC)
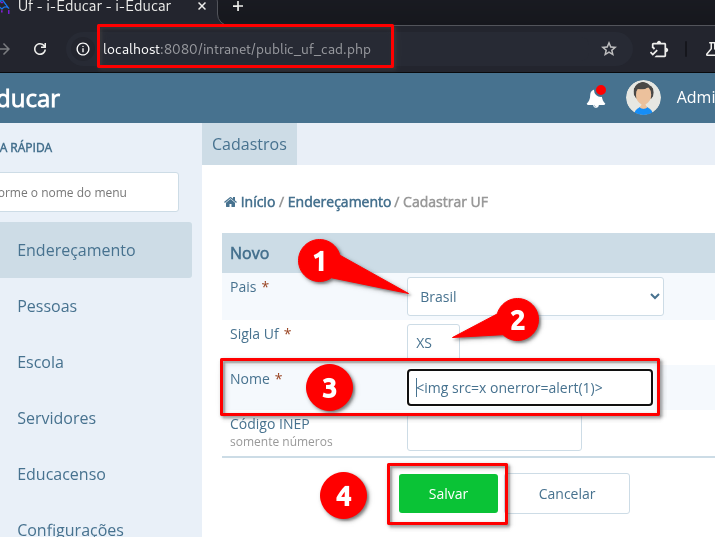
To reproduce this vulnerability, follow the steps below:
➤ Access the endpoint: /intranet/public_uf_cad.php
➤ Select “Brasil” in the first field (“País”)
➤ Choose any option in the second field (“Sigla Uf”)
➤ Insert the payload in the third field: Nome
➤ Click on: “Salvar”
The page
/intranet/public_uf_lst.phpwill be triggered automatically, executing the XSS:
Parameter nome |
|---|
 |
You can read the full technical report here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The issue was responsibly disclosed and registered as:
Conclusion
CVE-2025-8541 is another clear example of how improperly validated input can pose a significant security threat. In this case, even a simple field like “State Name” was enough to allow persistent XSS attacks.Extra care must be taken with administrative interfaces, and developers should enforce strict input sanitization across all user-facing fields — regardless of their perceived importance.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜