CVE-2025-8540

Stored XSS in i-Educar via public_municipio_cad.php (With PoC and Screenshots)
🇧🇷 Ler em Português.
CVE-2025-8540
Introduction
While reviewing yet another section of the i-Educar project, I discovered another instance of stored XSS — this time in the endpoint /intranet/public_municipio_cad.php. The vulnerability lies in the nome parameter, which doesn’t properly sanitize user input, allowing scripts to be injected and persist in the system.Once saved, the payload is executed automatically when the listing page is accessed. The issue was formally recognized as CVE-2025-8540.In this post, I walk you through the technical details, the step-by-step PoC, and the real risks this bug presents in production.
What is CVE-2025-8540?
CVE-2025-8540 is a stored Cross-Site Scripting (XSS) vulnerability affecting the /intranet/public_municipio_cad.php endpoint of the i-Educar application.The flaw resides in the nome parameter, which accepts and stores malicious input without any validation or sanitization.The script is triggered automatically when users access the listing page: /intranet/public_municipio_lst.php.
Technical Details
➤ Vulnerable Endpoint: /intranet/public_municipio_cad.php
➤ Affected Parameter: nome
➤ Trigger Page: /intranet/public_municipio_lst.php
➤ Payload Used
<img src=x onerror=alert(1)>
Proof of Concept (PoC)
To reproduce the vulnerability, follow these steps:
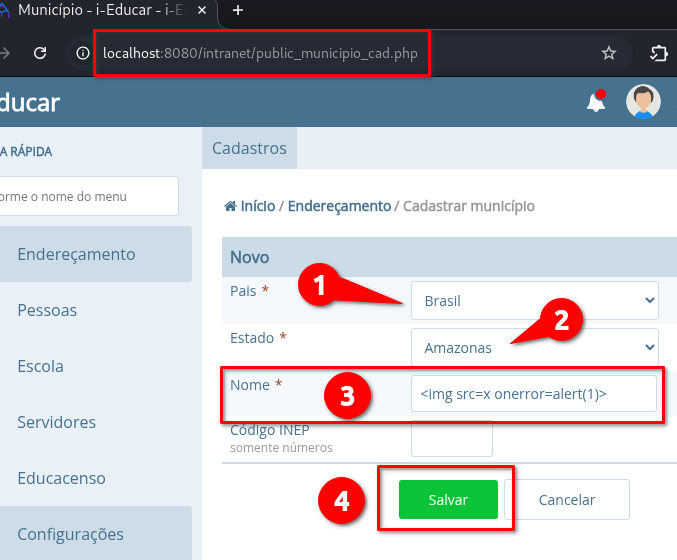
➤ Access the endpoint: /intranet/public_municipio_cad.php
➤ Select “Brasil” in the first field (“País”)
➤ Choose any option in the second field (“Estado”)
➤ Insert the payload in the third field: Nome
➤ Click on: “Salvar”
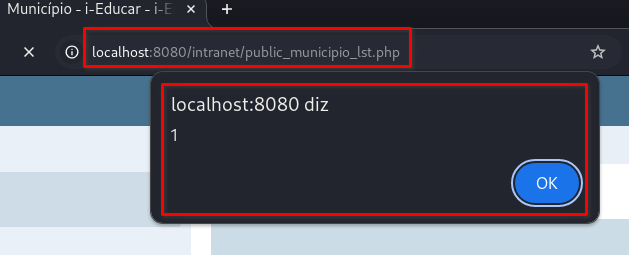
The page
/intranet/public_municipio_lst.phpwill load immediately, and the stored XSS will execute automatically:
Parameter nome |
|---|
 |
You can access the full report and see the complete step-by-step here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The vulnerability was reported ethically and assigned as:
Conclusion
This is another example of how a single unsanitized field can create a serious security threat. CVE-2025-8540 serves as a reminder of the importance of proper input validation — especially in administrative sections of web applications.If you work with systems handling public data, educational platforms, or user-generated content, always review every input field — no matter how small — to avoid this kind of persistent threat.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜