CVE-2025-8538

How I Discovered Multiple Stored XSS Flaws in i-Educar (With PoC and Screenshots)
🇧🇷 Ler em Português.
CVE-2025-8538
Introduction
While I was analyzing the Open-Source project i-Educar, I stumbled upon something unexpected: a stored XSS vulnerability that could silently affect anyone using the system. And it wasn’t just one field — both the name and description parameters in the /usuarios/tipos/novo route were vulnerable.After properly testing, documenting, and reporting the issue, it was officially assigned as CVE-2025-8538.In this post, I’ll show you how I found the flaw, how it works, and why it matters — with real screenshots, a working PoC, and the impact this kind of bug can have in production environments.
What is CVE-2025-8538?
CVE-2025-8538 indicates two stored Cross-Site Scripting (XSS) vulnerabilities in the /usuarios/tipos/novo endpoint of the i-Educar application.The vulnerability allows attackers to inject malicious scripts into the name and description fields.These scripts are saved on the server and executed as soon as the /usuarios/tipos page is loaded. This means that any user who accesses that page ends up executing the script without noticing.
Technical Details
➤ Vulnerable Endpoint /usuarios/tipos/novo
➤ Affected Parameters: name, description
➤ Trigger Page: /usuarios/tipos
➤ Payload Used
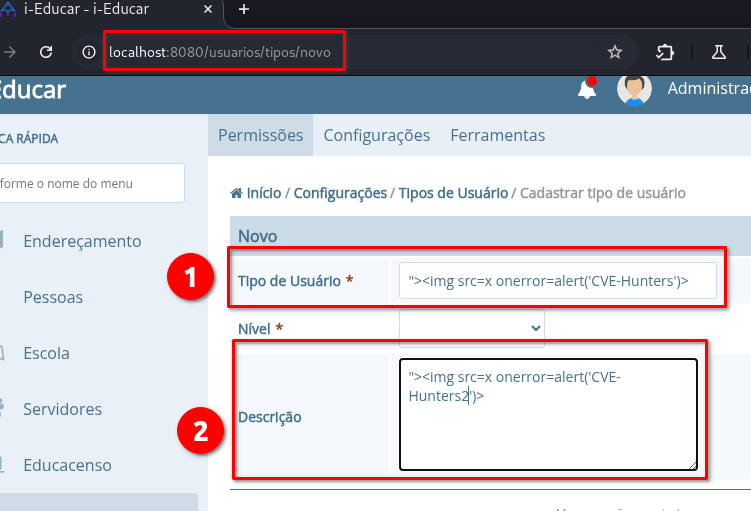
"><img src=x onerror=alert('CVE-Hunters')>
Proof of Concept (PoC)
To demonstrate the vulnerability, the following steps were performed:
➤ Access the endpoint: /usuarios/tipos/novo
➤ Insert the payload above into the fields: Tipo de Usuário e Descrição
➤ Click on: “Salvar”
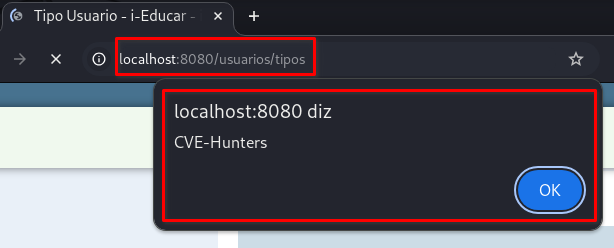
The
/usuarios/tipospage will automatically load, triggering the XSS:
Parameter name | Parameter description |
|---|---|
 | 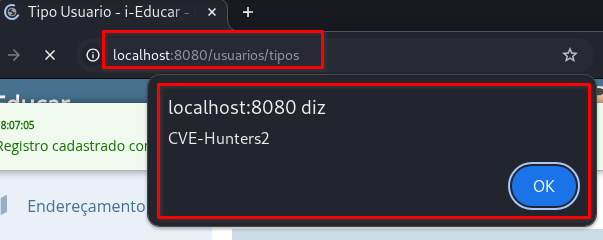 |
You can access the full report and see the complete step-by-step here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The vulnerability was reported ethically and assigned as:
Conclusion
This discovery reinforces the importance of input validation and the adoption of secure coding practices in web development. Even educational systems — which handle sensitive data from students and teachers — are not immune to critical vulnerabilities.If you’re a developer, sysadmin, or security enthusiast, here’s a reminder: never underestimate the impact of a stored XSS vulnerability.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜