CVE-2025-10909

Stored XSS via SVG Upload Bypass in NovoSGA
🇧🇷 Ler em Português.
CVE-2025-10909
Introduction
What if simply uploading an SVG file could compromise a user’s browser? In this post, I’ll walk you through a stored XSS vulnerability I discovered in NovoSGA that leverages a file upload bypass to inject and execute JavaScript.This vulnerability was assigned CVE-2025-10909 after responsible disclosure and affects the logoNavbar and logoLogin parameter of the /admin endpoint.Below you’ll find the technical details, a step-by-step PoC, payloads, impact, and official references.
What is CVE-2025-10909?
CVE-2025-10909 is multiples Stored Cross-Site Scripting (XSS) vulnerability triggered through SVG file upload bypass. Unlike traditional input-based XSS, this flaw allows an attacker to upload a malicious SVG containing embedded JavaScript. When rendered by the browser, this script executes automatically, compromising any user who accesses the file.This type of issue is especially dangerous because it persists on the server and doesn't require user interaction beyond simply visiting the file's URL.
Technical Details
➤ Vulnerable Endpoint /admin
➤ Affected Parameters: logoNavbar and logoLogin
➤ Trigger Pages: /uploads/logo-navbar.svg?_=[ID] and /uploads/logo-login.svg?_=[ID]
➤ Payload Used
<svg xmlns=""http://www.w3.org/2000/svg"" fill=""none""> <script> alert(""This is an XSS-POC from CVEHUNTERS""); </script> </svg>
Proof of Concept (PoC)
Here’s how you can reproduce the vulnerability step by step:
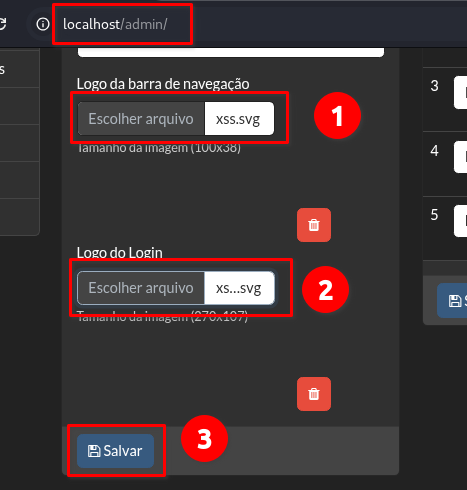
➤ Save the payload as: xss.svg
➤ Go to vulnerable endpoint
➤ Click “Escolher arquivo” (Choose File) and select xss.svg. Then, click “Salvar”
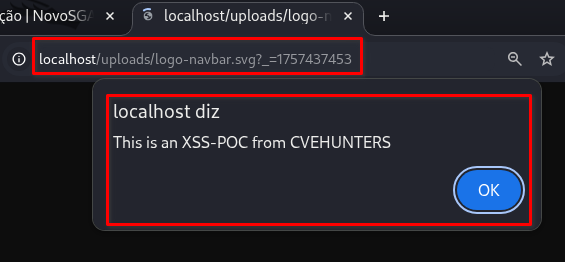
➤ Navigate to the trigger pages
The script will execute immediately.
Parameter logoNavbar | Parameter logoLogin |
|---|---|
 | 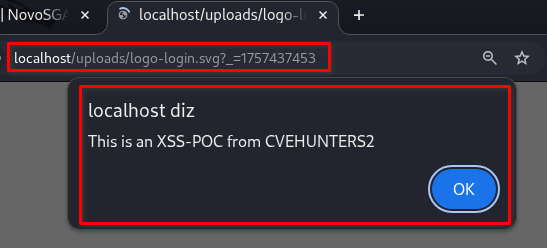 |
You can access the full report and see the complete step-by-step here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The vulnerability was reported ethically and assigned as:
Conclusion
Bypassing file upload restrictions using SVG files is a well-known XSS vector, yet still often underestimated. CVE-2025-10909 demonstrates how a seemingly harmless image upload can turn into a persistent client-side threat.Security teams should treat SVGs as active content, sanitize thoroughly, and avoid rendering user-uploaded files directly in the browser without filtering. Even one field — or file — is enough to compromise an application.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜