CVE-2025-10584

How I Discovered Multiple Stored XSS in i-Educar via educar_calendario_anotacao_cad.php (With PoC and Screenshots).
🇧🇷 Ler em Português.
CVE-2025-10584
Introduction
While analyzing the calendar registration functionality in the i-Educar system, I found multiple stored XSS vulnerabilities in the /intranet/educar_calendario_anotacao_cad.php endpoint. Both the nm_anotacao and descricao fields accepted malicious scripts without any input sanitization.As a result, the payload was saved on the server and executed automatically when accessing the calendar listing page. This vulnerability was officially assigned as CVE-2025-10584.In this post, I’ll walk you through the technical details, PoC steps, and security risks posed by this issue.
What is CVE-2025-10584?
CVE-2025-10584 refers two stored Cross-Site Scripting (XSS) vulnerabilities in the /intranet/educar_calendario_anotacao_cad.php endpoint of the i-Educar application.The nm_anotacao and descricao parameters fail to properly sanitize user input, allowing malicious scripts to be stored and automatically executed when the /intranet/educar_calendario_anotacao_lst.php page is accessed.
Technical Details
➤ Vulnerable Endpoint /intranet/educar_calendario_anotacao_cad.php
➤ Affected Parameters: nm_anotacao and descricao
➤ Trigger Page: /intranet/educar_calendario_anotacao_lst.php
➤ Payload Used
"><img src=x onerror=alert('CVE-Hunters')>
Proof of Concept (PoC)
To reproduce this vulnerability, follow the steps below:
1. Access vulnerable endpoint and click on "Novo Calendário Letivo".
2. In the new page, click on "Nova Anotação".
3. Insert the payload in first field ("Anotação") and second field ("Descrição").
4. Click on "Salvar".
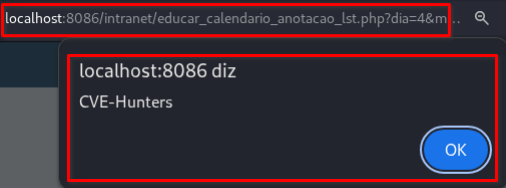
The
/intranet/educar_calendario_anotacao_lst.phppage will load automatically, triggering the stored XSS:
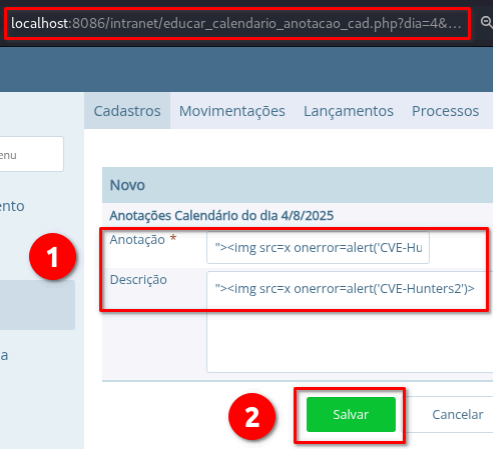
Parameter nm_anotacao | Parameter descricao |
|---|---|
 | 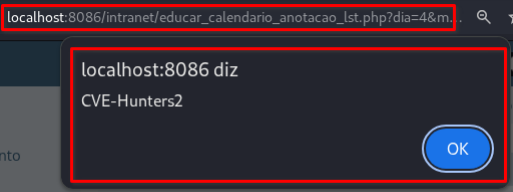 |
You can access the full technical report with all PoC steps here:
Impact
This Cross-Site Scripting (XSS) vulnerability can be exploited to:
- Steal session cookies (session hijacking);
- Install malware on victims’ devices;
- Steal credentials stored in the browser;
- Redirect users to malicious websites;
- Deface the application interface;
- Damage the institutional reputation.
Official Sources
The issue was ethically reported and officially registered as:
Conclusion
CVE-2025-10584 shows that even seemingly harmless fields like company nm_anotacaos can become vectors for stored XSS attacks. When displayed in administrative panels without proper validation or output encoding, they pose a real threat.Ensuring input validation on every form — no matter how trivial the field — is important to keeping web applications secure.
Credits
Discovered with💜 by Karina Gante.
Official Member of CVE-Hunters🏹
Related Content

If you find this post helpful, please consider sharing 💜